Basically Linux kernel update would require system reboot. New kernel doesn’t take effect until we reboot the system.
On average, the Linux kernel receives security updates and bug fixes mostly once in a month.
For critical system we can’t schedule downtime every month because it may have many dependencies and we wont get approval from management.
How to overcome this? Yes, we have the option in Oracle Premier Support. It is called Ksplice.
What is Ksplice
Oracle Ksplice enables you to keep your systems secure and highly available by allowing you to update your systems with the latest kernel security errata and other critical updates.
It updates the running kernel image without requiring a reboot. It updates your running kernel in memory. A Ksplice update takes effect immediately it is applied. It is not an on-disk change that only takes effect after a subsequent reboot.
- kpatch allows Red hat, CentOS and Fedora users to install kernel security patch without rebooting
Make sure your system should registered with Unbreakable Linux Network (ULN) in order to use Ksplice. You can opt to use Oracle Ksplice if you have an Oracle Linux Premier Support account.
Refer the following url to register the system with Unbreakable Linux Network (ULN).
Once you done registration with Unbreakable Linux Network (ULN) then subscribe your systems to the Ksplice for Oracle Linux channel and install the Ksplice Uptrack software on them.
How to register the system to use Oracle Ksplice on ULN
If you already have an account on ULN, you can register your system to use Ksplice Uptrack.
Login to ULN @ http://linux.oracle.com.
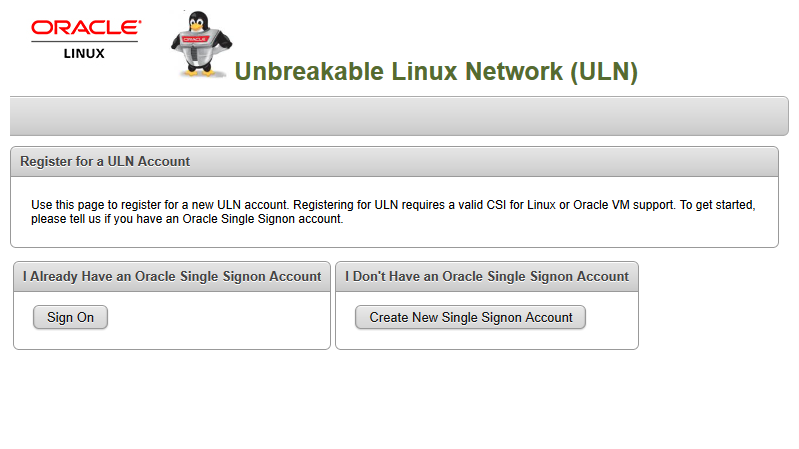
Click Ksplice Uptrack Registration button in ULN home page and select Customer Support Identifiers (CSIs) that you want to use and click Register.
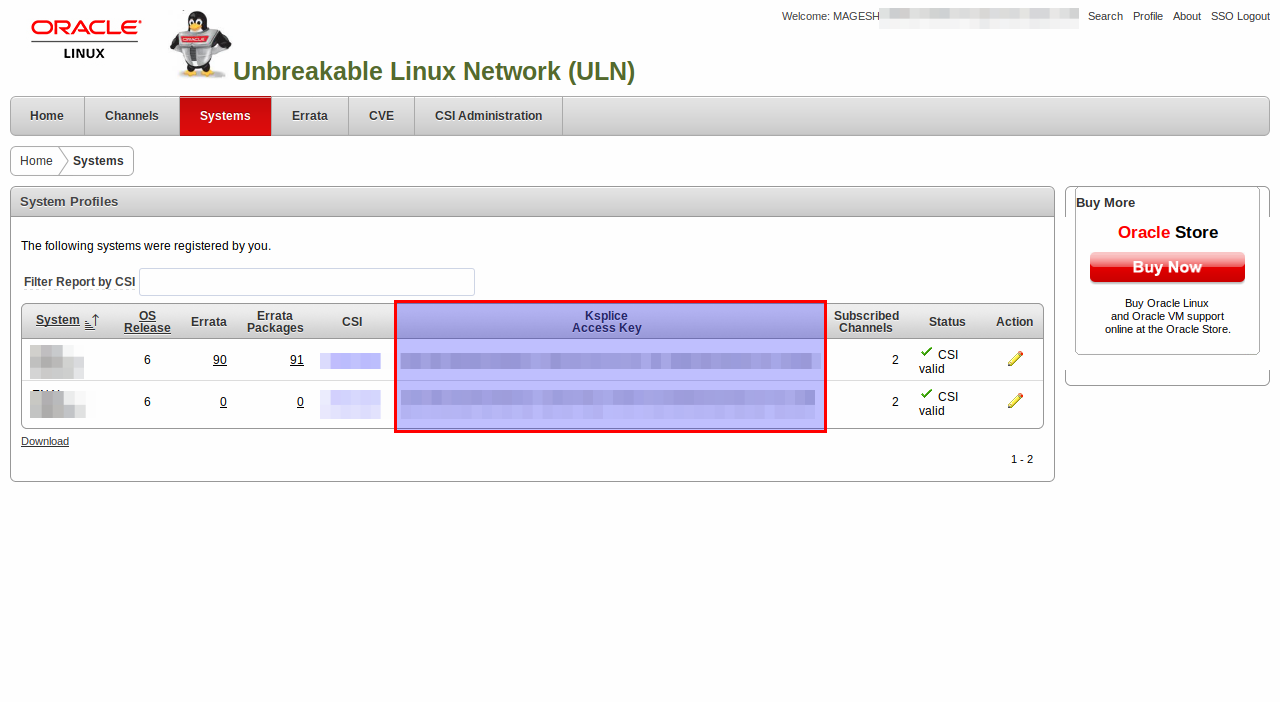
The screen displays an acknowledgment that a Ksplice account has been created and that an e-mail containing the Ksplice access key.
The same has been verified through ULN portal.
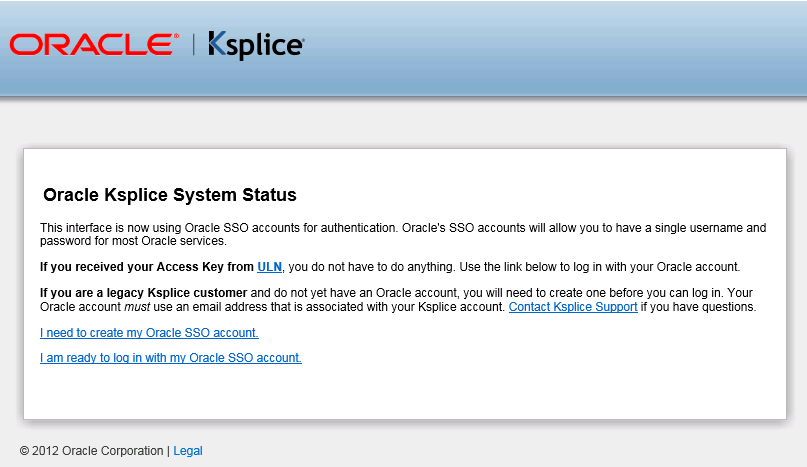
Use Oracle SSO account to log into the Ksplice web interface at https://status-ksplice.oracle.com/ and register the systems.
There is no system registered as of now. The same has been verified in the below screenshot.
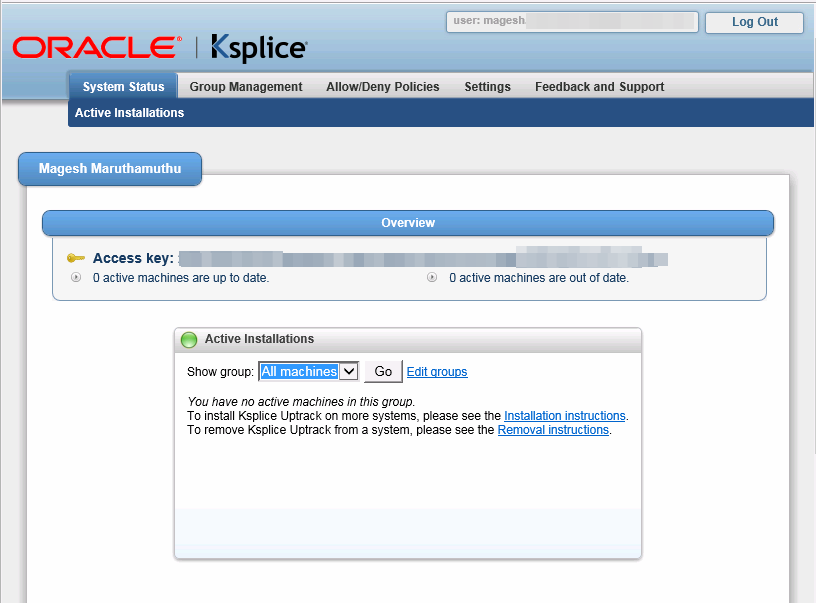
How to install Ksplice Uptrack
Just run the following commands to install Ksplice Uptrack. Make sure you have to run the following commands as root.It offers installer script so, run the following commands as root and replace YOUR_ACCESS_KEY with your access key.
If you would like to enable automatic updates then set autoinstall = yes in /etc/uptrack/uptrack.conf file after installation.
# wget -N https://www.ksplice.com/uptrack/install-uptrack # sh install-uptrack YOUR_ACCESS_KEY
Alternatively we can add --autoinstall option in the install-uptrack command.
# sh install-uptrack YOUR_ACCESS_KEY --autoinstall
By default, Ksplice Uptrack will reinstall rebootless updates during the boot process so you remain secure even after a reboot. You can configure this behavior by changing the install_on_reboot option in /etc/uptrack/uptrack.conf.
# vi /etc/uptrack/uptrack.conf install_on_reboot = [no or yes]
Yes, now we can able see the list of registered systems.
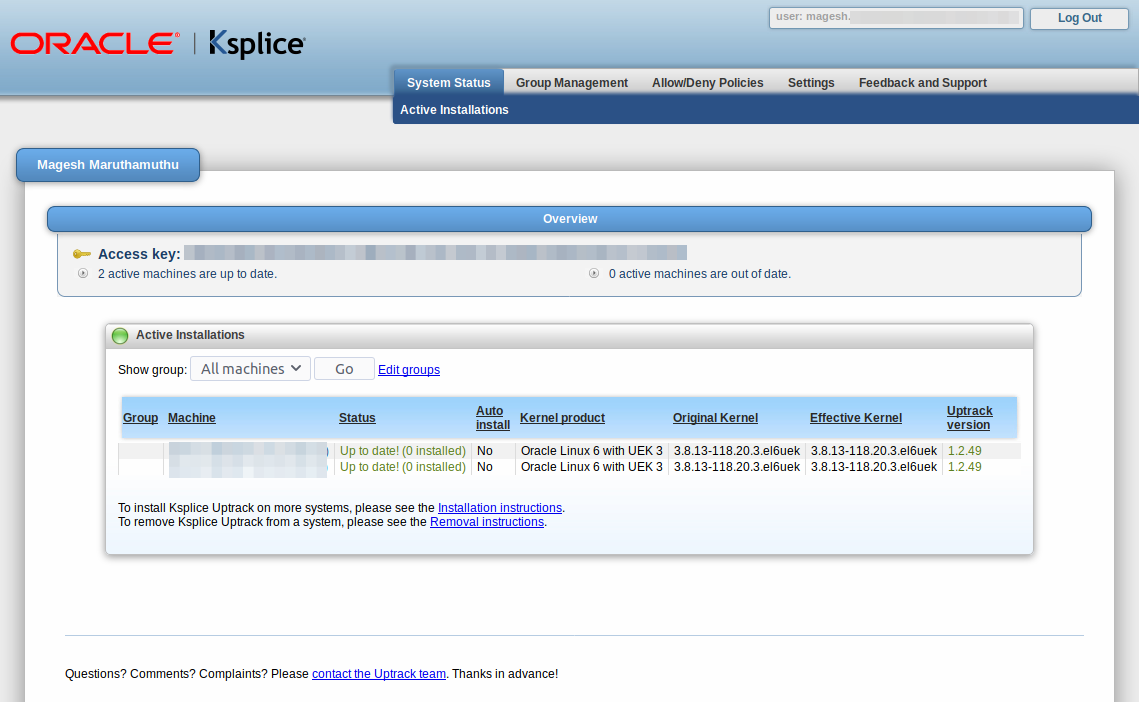
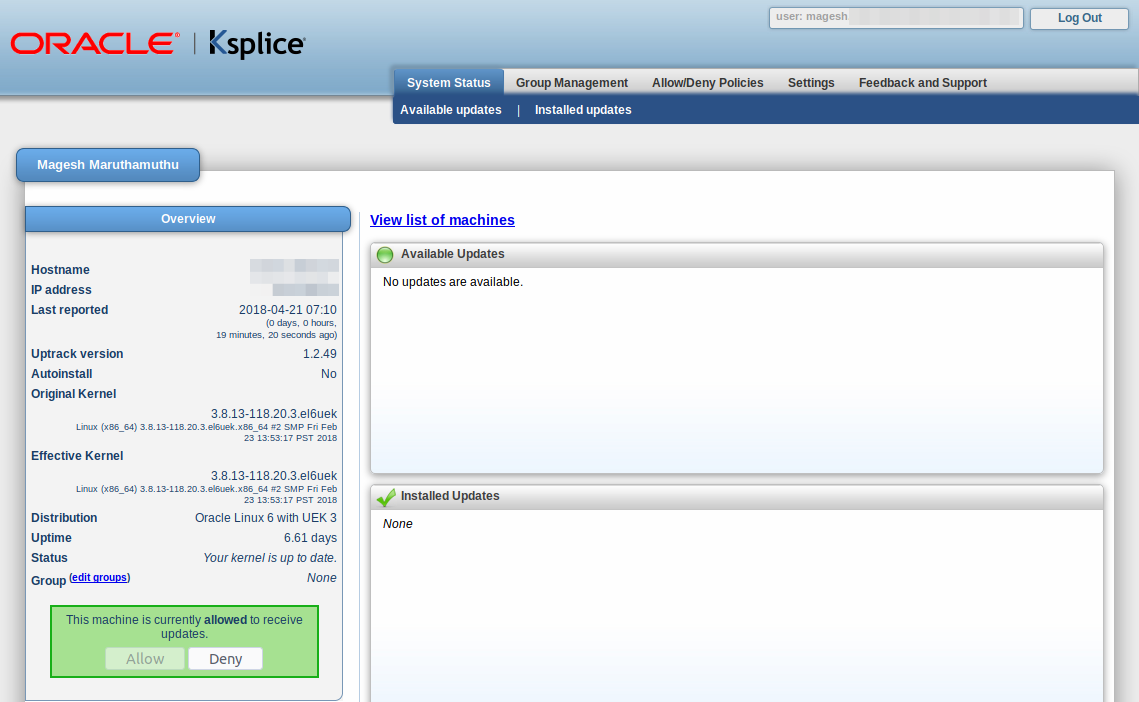
To view available updates & installed updates.
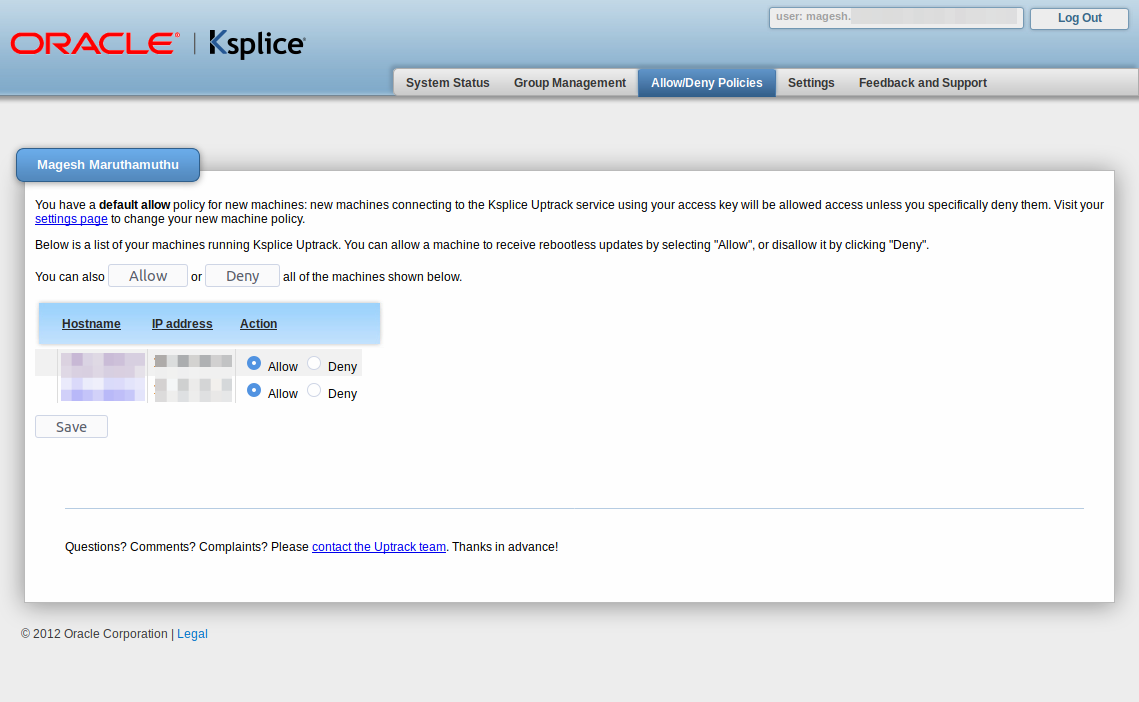
Use the below page to Allow or Deny system to use ksplice uptrack.
To list the available Ksplice updates, use the following uptrack-upgrade commands.
# uptrack-upgrade -n or # uptrack-show --available Available updates: [fiq04xbb] CVE-2013-2237: Information leak on IPSec key socket. [9q4luou3] CVE-2014-3687: Remote denial-of-service in SCTP stack.
To install all available Ksplice updates.
# uptrack-upgrade -y The following steps will be taken: Install [guclwyc2] CVE-2012-0957: Information leak in uname syscall. Install [j4d07e02] Kernel panic in IPv4 ARP and IPv6 Neighbor Discovery. Install [r8og1ec4] CVE-2013-1979: Privilege escalation with UNIX socket credentials. Install [fiq04xbb] CVE-2013-2237: Information leak on IPSec key socket. Install [9q4luou3] CVE-2014-3687: Remote denial-of-service in SCTP stack. Installing [guclwyc2] CVE-2012-0957: Information leak in uname syscall. Installing [j4d07e02] Kernel panic in IPv4 ARP and IPv6 Neighbor Discovery. Installing [r8og1ec4] CVE-2013-1979: Privilege escalation with UNIX socket credentials. Installing [fiq04xbb] CVE-2013-2237: Information leak on IPSec key socket. Installing [9q4luou3] CVE-2014-3687: Remote denial-of-service in SCTP stack. Your kernel is fully up to date. Effective kernel version is 3.8.13-118.20.3.el6uek
To view installed updates.
# uptrack-show Installed updates: [guclwyc2] CVE-2012-0957: Information leak in uname syscall. [j4d07e02] Kernel panic in IPv4 ARP and IPv6 Neighbor Discovery. [r8og1ec4] CVE-2013-1979: Privilege escalation with UNIX socket credentials.
After ran uptrack-upgrade command we can see the effective kernel a machine is running. Ksplice Uptrack does not change the output of uname. Run uptrack-uname to see the updated running kernel on machine.
# uname -r 3.8.13-68.2.2.el6uek # uptrack-uname -r 3.8.13-118.20.3.el6uek
To remove all updates from the kernel.
# uptrack-remove -y or # uptrack-remove --all The following steps will be taken: Remove [guclwyc2] CVE-2012-0957: Information leak in uname syscall. Remove [j4d07e02] Kernel panic in IPv4 ARP and IPv6 Neighbor Discovery. Remove [r8og1ec4] CVE-2013-1979: Privilege escalation with UNIX socket credentials. Remove [fiq04xbb] CVE-2013-2237: Information leak on IPSec key socket. Remove [9q4luou3] CVE-2014-3687: Remote denial-of-service in SCTP stack.
To Uninstall Uptrack.
# yum -y remove uptrack



